For the Remote Desktop Manager SSH client to be compliant with the FIPS 140-2 annex A standard, you need to apply specific configuration changes in Remote Desktop Manager options.
To be compliant, you must ensure that non-compliant algorithms are disabled. To do this, you need to verify that the boxes that are NOT checked in the screenshots below are disabled in the client configuration.
We do not recommend using these settings unless you are in an environment that requires compliance with the FIPS 140-2. Most users should stick to the default settings of Remote Desktop Manager and enable additional cipher suites only if required by their servers.
These values originate from the Microsoft’s documentation FIPS140.2 annex A standard
Settings
- In Remote Desktop Manager, go to File – Settings – Types – Terminal – Algorithm Support.
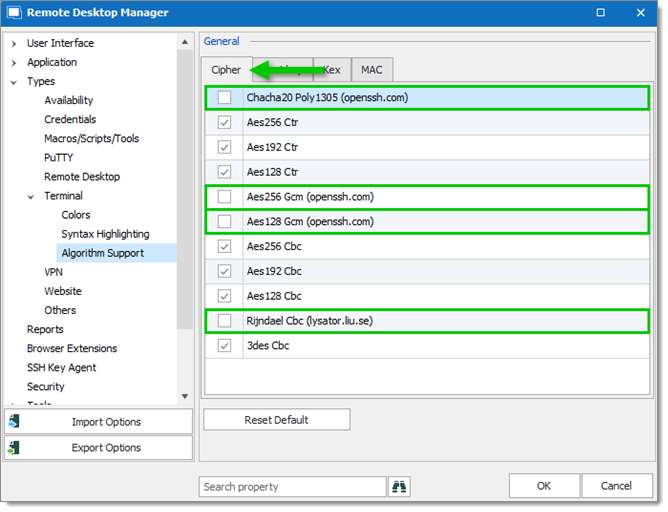
- In the Cipher tab, uncheck:
- Chacha20 Poly1305 (openssh.com)
- Aes256 Gcm (openssh.com)
- Aes128 Gmc (openssh.com)
- Rijndael Cbc (lysator.liu.se)
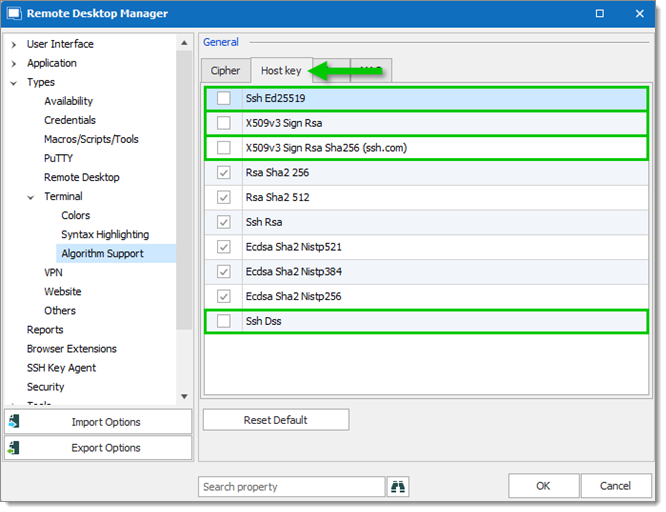
- In the Host key tab, uncheck:
- Ssh Ed25519
- X509v3 Sign Rsa
- X509v3 Sign Rsa Sha256 (ssh.com)
- Ssh Dss
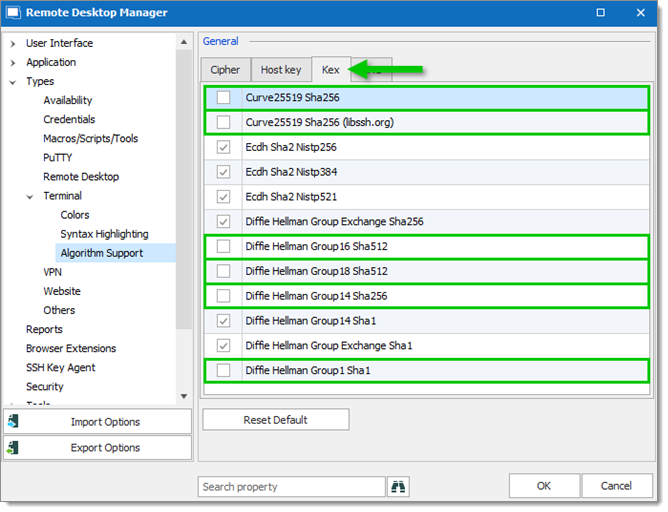
- In the Kex tab, uncheck:
- Curve25519 Sha256
- Curve25519 Sha256 (libssh.org)
- Diffie Hellman Group16 Sha512
- Diffie Hellman Group18 Sha512
- Diffie Hellman Group14 Sha256
- Diffie Hellman Group1 Sha1
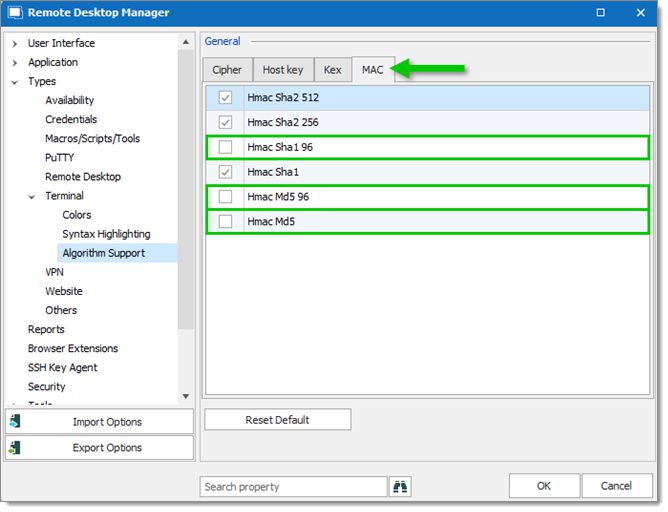
- In the MAC tab, uncheck:
- Hmac Sha 1 96
- Hmac Md5 96
- Hmac Md5
- Click OK.




